- Activant's Greene Street Observer
- Posts
- The Long Road to Automating the SOC
The Long Road to Automating the SOC
Why it’s time to shift the focus to acceleration

Introduction
It’s past midnight. The Security Operations Center (SOC) analyst on duty checks his screen: “Suspicious login attempt… phishing email flagged… malware detected on an endpoint.” His organization has invested in a highly sophisticated security platform built from best-of-breed tools, all flagging issues for the SOC to remediate. Bleary-eyed, scanning a sea of red indicators, the SOC analyst is drowning in alerts. Unfortunately, this is not the start of a work of fiction – the average SOC team receives four and a half thousand alerts, every day.
What’s needed is a system that can intelligently filter, prioritize, and remediate alerts. However, from SIEMs (Security Information and Event Management) to SOARs (Security Orchestration, Automation, and Response) and beyond, threat volumes have consistently risen faster than these systems can handle. The result is that despite all these tools, SOC analysts are bogged down in repetitive, manual processes. Automation helps with only 17% of alerts, leaving SOC analysts with too many low-quality alerts to possibly sift through. Consequently, 67% of these alerts are ignored completely, making it no surprise that we read about new breaches on an almost daily basis.
In this article, we ask why SOC tools often fall short and how pragmatic AI combined with targeted workflow automation can shift us from ‘autonomous’ hype to action. The goal: an accelerated SOC with less grunt work and fewer breaches. Let’s dive in.
What’s a SOC?
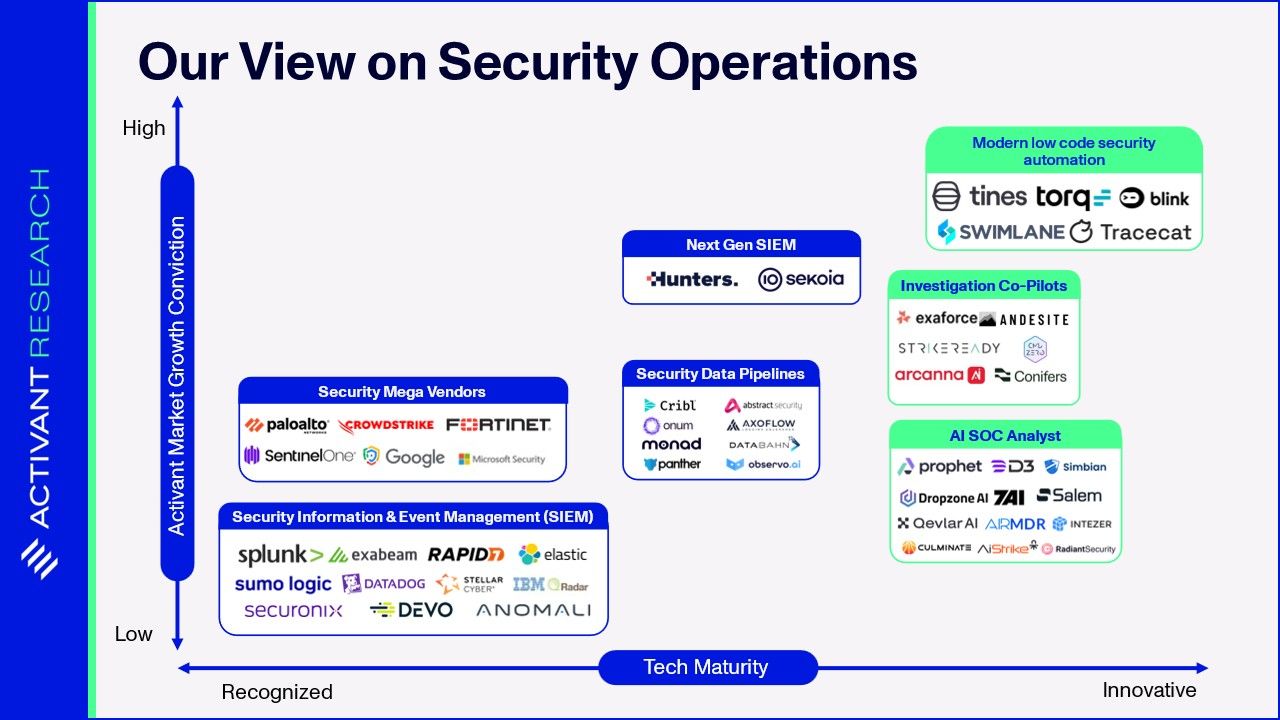
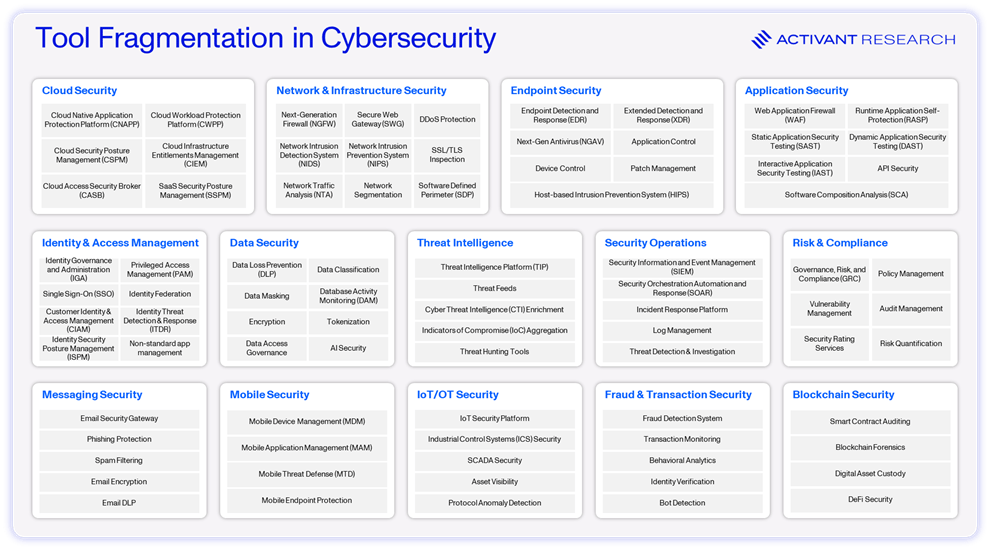
Modern IT sprawls across many surfaces: cloud and on-prem, SaaS and internally developed applications. Vulnerabilities can arise in networks, endpoint devices, internal code, and even the configurations of cloud resources. To address this, security tools have similarly proliferated to cover these expanding attack surface. As we can see below, the ecosystem of security tools has become highly fragmented, with the average team now using as many as 50 different tools. The key issue is that each of these systems generates its own security alerts. Managing this fragmented landscape in a systematic way is what gave rise to the SOC.
The SOC centralizes the security management function to bring order to this chaos. Beyond real-time monitoring, the SOC is tasked with threat analysis, incident response, prevention, and management of the full security tooling stack. Performance is often measured by how quickly it can detect and remediate threats, as well as how well it minimizes system downtime and business disruption. While large enterprises often run in-house SOCs, many smaller firms outsource the function to Managed Security Service Providers (MSSPs) or run a combined security/IT team.
Today the SOC is all about humans – manpower-heavy and organized in tiers:
Tier 1 Analysts, or Triage Specialists, act as the first line of defense – monitoring alerts, performing initial triage, and escalating serious incidents.
Tier 2 Analysts, or Incident Responders, take over escalated cases to conduct deeper investigations, correlate data, hunt for threats, and develop new detection use cases.
Tier 3 Analysts, or Threat Hunters, handle the most complex threats, lead proactive threat hunting, oversee vulnerability assessments, and fine-tune security tools to enhance the SOC’s overall effectiveness.
Below, we visualize the SOC process flow, and the key tools utilized to get the job done.
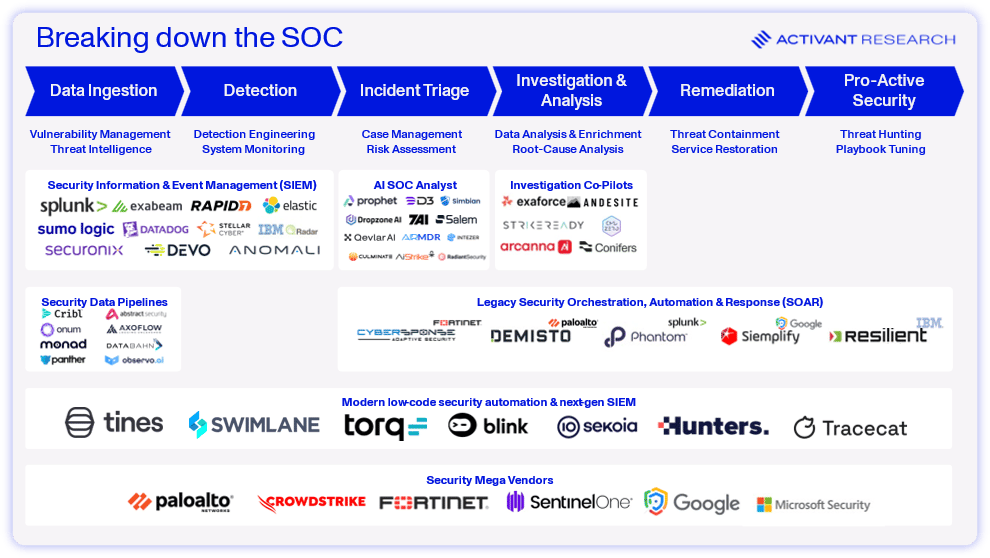
In theory, this seems like a sensible and effective approach to managing security operations. In practice, it’s a disaster.
SOCs Suck
Piping every security alert from across an entire organization into a small team (normally 2 - 10 people) produces some unfortunate but predictable problems, namely alert fatigue, tool overload, and staffing issues.
Alert Fatigue: A typical SOC faces 4,500 alerts daily, and at Fortune 100s, the number runs into the millions. Most alerts are repetitive, low fidelity “noise” but must be cleared manually. Analysts believe that at least half of their tasks could be automated. Worse still, somewhere between 50% and 99% of these alerts are false positives – alerts which turn out to be benign when investigated. Imagine starting your morning with the impossible task of sifting through thousands of repetitive events, knowing most will be a waste of time. Analysts get desensitized, demotivated, and miss true threats hiding in the noise – it’s no surprise then that up to 67% of alerts are completely ignored.
Tool Overload: For the average security team, resolving alerts requires gathering context and taking action across 50 different security tools. Swivel chair syndrome, as it is unaffectionately known in the industry, makes it even harder to make critical decisions and stay productive. Further, it can be extremely costly to build and maintain the connections required to string these tools together, so they often remain siloed. This lack of visibility into enterprise IT ranks among the top 5 challenges SOCs face.
Staffing issues: The total security industry employs an estimated 5.5 million people yet declares a workforce gap of ~4mn. On average, every security employee is doing the work of ~1.7. Unsurprisingly, many believe that burnout and attrition is highest in security staff.
The result: fatigued, short-staffed SOC teams without the right tools at their disposal. It’s no wonder SOCs underperform in preventing, detecting and responding to actual breaches. There were over 10,000 reported breaches in 2024; and more alarmingly, the average enterprise takes an average of 287 days to detect and respond to one of these. That’s right – many enterprises are carrying unresolved breaches for as long as a human pregnancy. The SOC is crying out for automation.
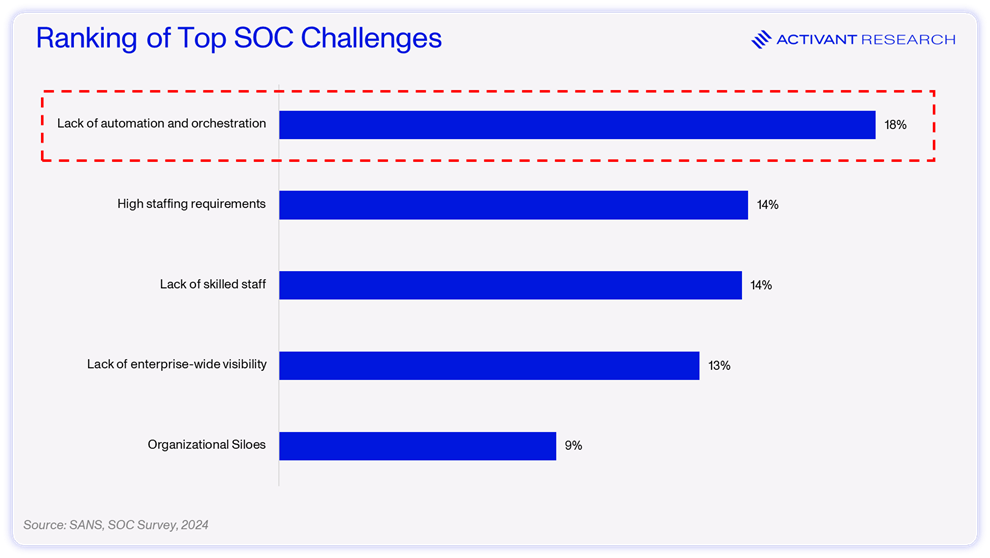
It’s not that no one has ever taken on the challenge of automating the SOC, but considering the statistics above, it’s evident that the status quo– the SIEM and SOAR combo – has failed.