- Activant's Greene Street Observer
- Posts
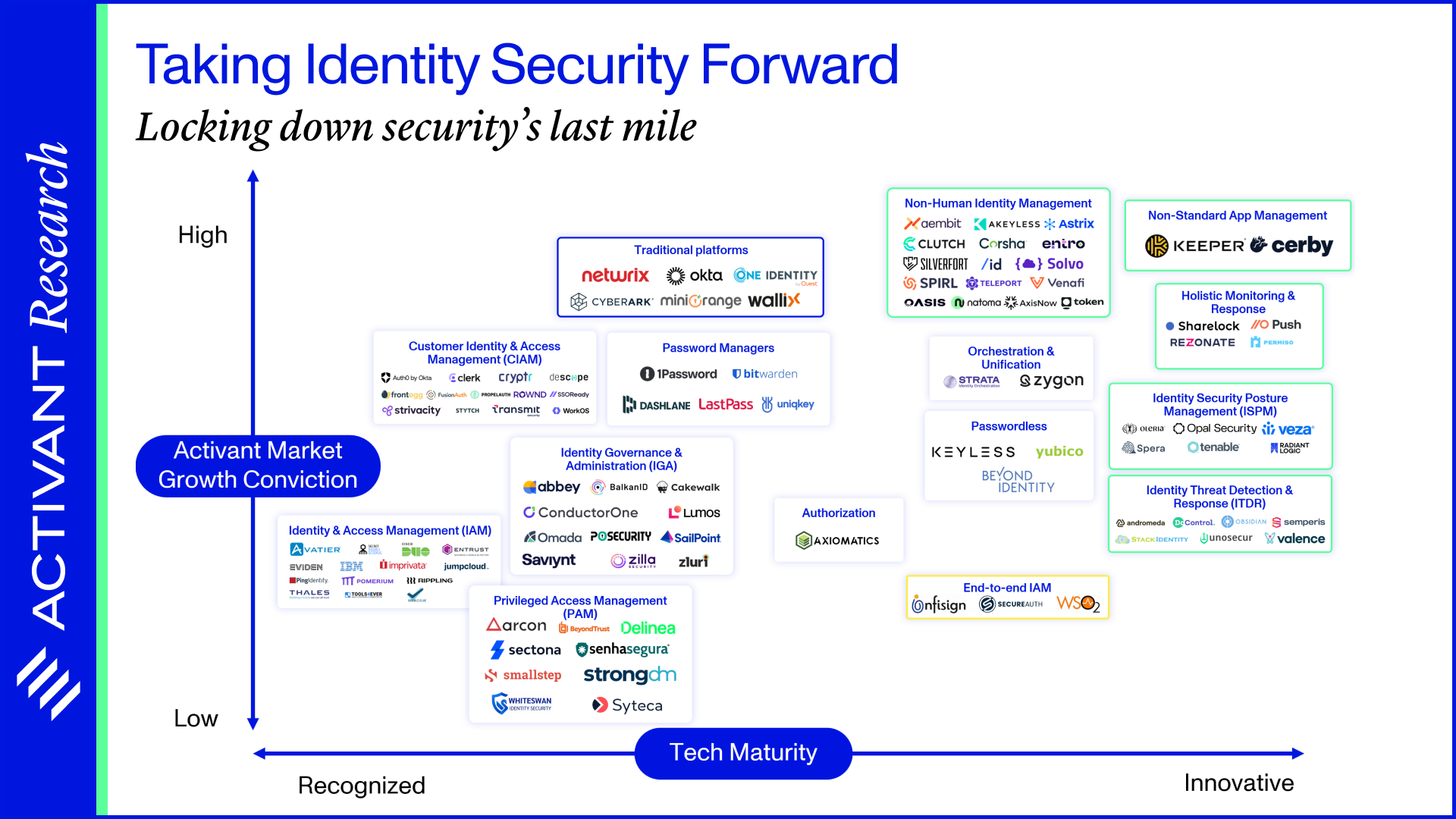
- Taking Identity Security Forward
Taking Identity Security Forward
Locking down security's last mile

Introduction
Modern supply chains are incredibly complex. An iPhone, for example, is assembled across multiple continents, comprising over 100 components that are sourced from more than 200 suppliers in 43 different countries. But with well-established standards and processes, it all just works. However, numerous challenges arise when transporting goods from local warehouses to the customer’s doorstep - the last mile. The supply chain’s last mile is often the most inefficient, unpredictable step and has the greatest impact on customer satisfaction. In cybersecurity, the same principles apply.
Cybersecurity is a $200 billion+ market, driven by substantial investments in firewalls, endpoint and cloud security. Despite these defenses, enterprises are left grappling with one critical question: who should have access? That’s Identity Security: it’s the last mile of cybersecurity and, just like the last mile of a supply chain, it is fraught with challenges. In fact, it is arguably the most fundamental weak point of modern cybersecurity. Two-thirds of all data breaches involve a “human element” (read: they leveraged identity) and 94% of organizations have suffered an identity-related breach. Hackers don’t hack in, they log in. That may be a cliché in the identity security industry, but it highlights the need to fix security’s last mile in order to solve the growing data breach problem.

In this report, we look at how companies are currently securing the last mile, examine how outdated infrastructure, non-human identities and non-standard apps are leaving cracks for attackers to exploit, and consider the start-ups that are emerging to solve these problems.
The New Perimeter
Historically, enterprise security relied on a perimeter-based strategy, with firewalls acting as moats to protect internal networks. Trust was implicitly granted to any device within the perimeter, often identified by IP addresses. However, this model proved deeply flawed: once an attacker breached the network, they gained unrestricted access to critical systems and data. More importantly, new ways of working obsoleted perimeter-based security. Pandemic-induced work-from-home policies pushed people outside of the network, and the shift to the cloud pushed data outside of it.
As a result, companies are rapidly shifting to the zero-trust security model where no actor receives implicit trust. Without implicit trust, every single actor must be explicitly authenticated and authorized to access any data or system. This shift makes identity one of the most foundational pieces of modern cybersecurity. Identity is the new perimeter.
As we’ve established the critical importance of identity security in the modern enterprise, let’s explore the infrastructure that enables the authentications and authorizations that zero-trust depends on.